What we do
Threat Protection solutions

























Don’t let cracks in your digital defence keep you up at night.
The ever-evolving threat landscape can keep you awake at night.
Malware, phishing, ransomware, and DDoS attacks pose significant risks to your organisation’s security.
Our threat protection solution, backed by Microsoft’s cutting-edge solutions, ensures you are well-prepared to combat any cyber threats, offering adaptability and intelligent protection.
Our services can help you:
-
Lower risk with continuous threat monitoring and hunting.
-
Respond rapidly with automated incident alerts and meaningful insights.
-
Save money by consolidating security into a single suite.
-
Stay compliant and avoid hefty fines and reputational damage.
Don’t let security nightmares become reality
As organisations rapidly transition to the Cloud, many find their systems are unable to safeguard their users and data. An ideal scenario for cyber criminals.
Your challenges:
Limited awareness
No understanding of what the latest threats are = no idea of your exposure levels.
Clouded vision
Disjointed solutions stop security teams from quickly seeing the entire threat chain.
Lack of integration
Fragmented solutions from different vendors prevent integrated, comprehensive protection.
Inefficiencies
SecOps teams waste precious time manually correlating signals across multiple solutions and portals.
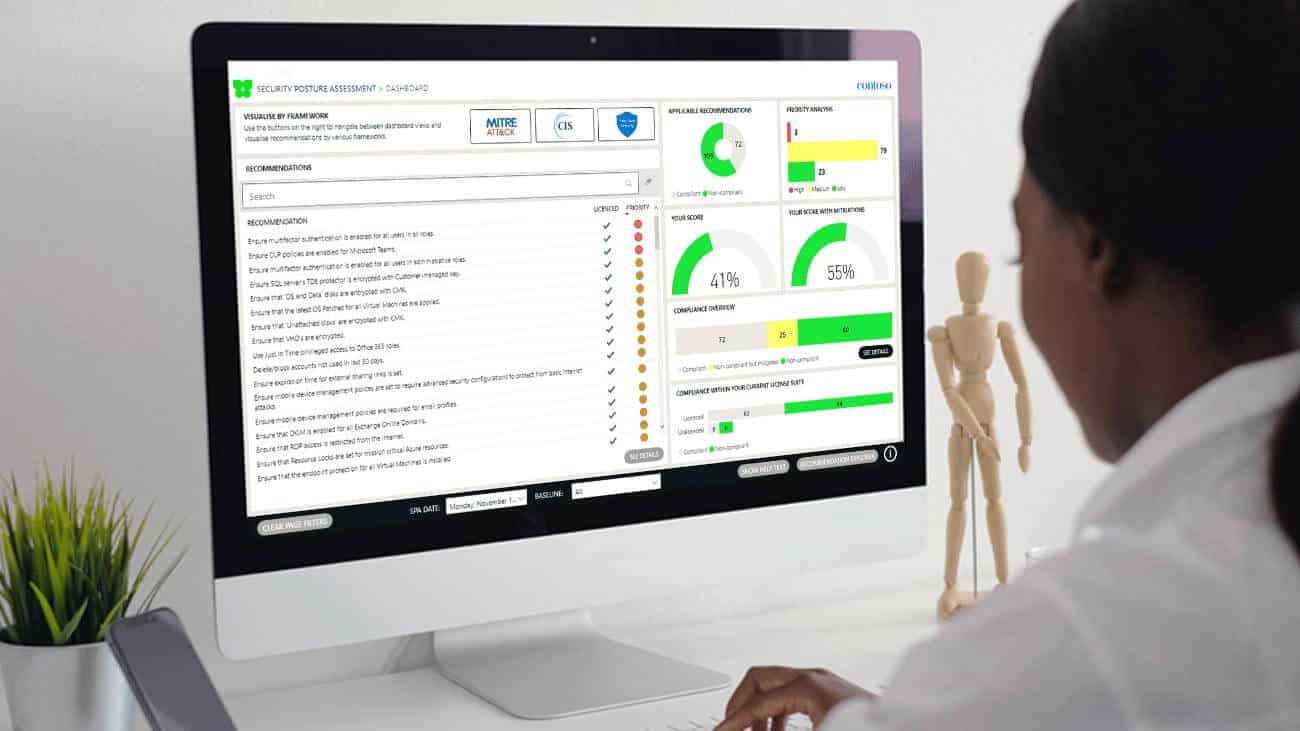
Watch 3-minute Security Posture Assessment Demo
Identify hidden threats and prioritise security risks.
Evidence has shown cyber criminals can go from initial entry to ransoming an entire network in less than 45 minutes.
Microsoft Digital Defense Report, September 2020
Powerful threat protection – clever, cutting-edge, comprehensive
Utilising Microsoft’s market-leading security solutions, we’ll enable your organisation to achieve its full potential by ensuring you’re ready for whatever attackers throw at you.
You’ll benefit from:
Security assessment
Understand your security position, identify gaps, and define a roadmap to resolve them.
Robust solution
Build a robust threat protection solution unique to your organisation’s challenges.
User protection
Keep your users productive and protected whenever and wherever they work
Latest security trends
Benefit from the latest security concepts, best practices, and technology developments.
A comprehensive threat protection solution tailored to your needs
Our solutions take care of:

Featured technology
Microsoft Security
Our threat protection solutions are developed using Microsoft’s industry-leading enterprise security technologies.
Microsoft’s natively integrated security toolset will ensure your team’s precious time is focused where it matters most.
Microsoft’s security suite is designed to help you achieve end-to-end visibility across all your resources, using AI to correlate and prioritise alerts, giving you greater context and automation capabilities.
The Security Posture Assessment has helped us immensely to visualise what is important and prioritise accordingly. The result has been a continuous delivery of enhancements to our security.
Paul Mathanarajah
Head of Infrastructure

Want to enhance your security?

Case studies
Who we've helped

A Stirling approach to advanced threat protection in the higher education sector


Creating a comprehensive cloud-based threat detection service for a global insurer





























In-house vs. outsourced security operations: Which is right for you?
Download your 35-page guide to discover:
- Costs and risks to build inhouse
- Potential security benefits and savings

Don't Miss
Great threat protection resources

Supercharge your security operations with SIEM and XDR

Achieving XDR: How to make your SIEM SOAR
Learn how a modern SOC based on the latest Microsoft Defender and Sentinel technologies can help you see and stop threats across your entire cloud and hybrid estate before they can do damage.

The ultimate guide to Microsoft Enterprise Security

Microsoft Sentinel vs. Splunk: Which is better?
Got a question? Need more information?
Our expert team is here to help.


